Types of social engineering
Social engineering is the broad term used to describe the myriads of tactics used by cyber criminals and fraudsters. It is the ways that they are fooling unsuspecting victims into performing an action that compromises their organisation’s security.
Including, but not limited to:
- Clicking on links
- Opening attachments
- Clicking unsafe URL’s
- Sending money to cyber attackers
- Disclosing sensitive information
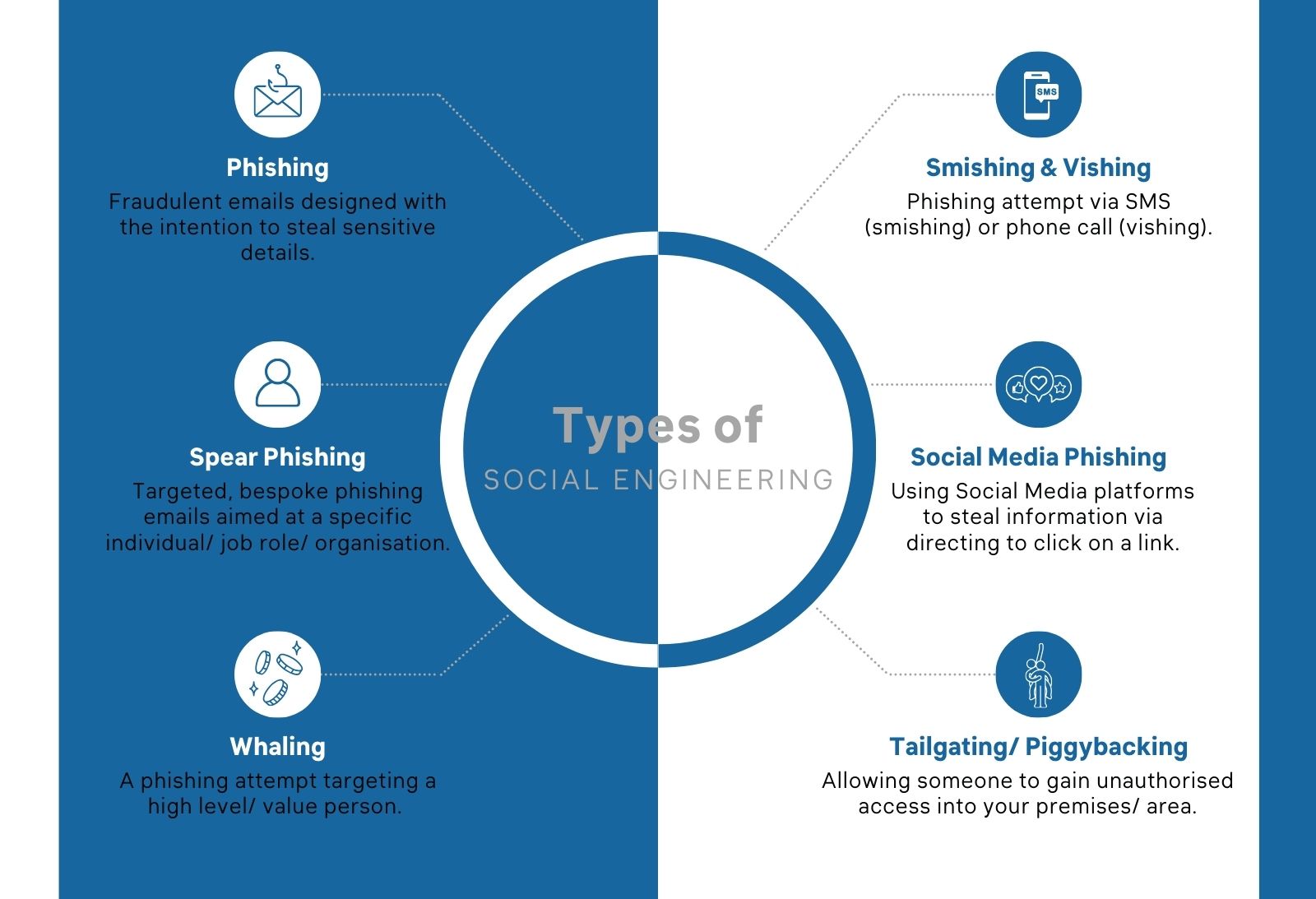
Some of the most common types of social engineering include:
- Phishing:
- Spear phishing
- Whaling
- Smishing & Vishing
- Social media phishing
- Tailgating/ Piggybacking
We’ll investigate these types of social engineering in further detail in today’s blog post, where we will provide you with an insight into how cyber criminals can manipulate your employees into gaining access into your systems.
Thus, compromising the security of those systems and your critical business and customer data.
Phishing:
Is the term given to a cyberattack where the criminals send fraudulent emails, messages or websites designed to trick the recipient into revealing sensitive information including usernames, passwords, credit card details.
The emails may appear to come from a trusted source such as bank, customer, mobile phone provider, or other services.
Spear phishing:
A more tailored type of phishing campaign where the criminals modify their message to a particular individual, often acquired from gathering personal information to make the attack attempt even more realistic, increasing the likelihood of success.
Whaling:
Whaling is another type of spear phishing which specifically targets a high profile, or high net worth individual, crafting sophisticated messages mimicking trusted colleagues or clients to deceive the target into divulging confidential or sensitive information or authorising financial transactions.
Smishing & Vishing:
These types involve SMS phishing (smishing) which involves sending fraudulent text messages that contain malicious links or requests for sensitive information. On the other hand voice phishing (vishing) which involves phone calls where the attacker impersonates legitimate companies (your bank, government etc.) Trying to trick victims into disclosing personal information, or encouraging them to make financial transactions.
Social media phishing:
This type of social engineering technique involves using social media platforms to deceive users into revealing personal details or clicking on malicious links.
Tailgating/ Piggybacking:
These two terms refer to physical security breaches where an authorised individual gains access by following someone with legitimate access into secure areas.
Tailgating means that the individual deliberately stays close to the authorised person in order to sneak in, whereas piggybacking refers to an individual gaining access with the autorised person knowingly or unknowingly allows them to enter.
Both forms of social engineering can lead to unauthorized access to sensitive areas or equipment.
Choose Data Installation & Supplies Ltd (DIS) to help safeguard your team from falling victim to social engineering attacks with our comprehensive security packages and targeted phishing simulations.
By being proactive and strengthening your team’s cyber security knowledge, you will be better protected and prepared for evolving cyber threats.
To discuss your specific business requirements, or to find out some more details about phishing any of our Security Professional Services please contact us on 01274 869 099 or fill out the contact form below and a member of our security team will contact you.
"*" indicates required fieldsEnquiry Form